Securing business email communications in Dubai demands tailored solutions compliant with UAE regulations while addressing advanced threats. Implement these three core strategies:
1. Select Compliance-First Hosting Providers
Mandatory UAE certifications are non-negotiable. Prioritize providers holding valid:
- TDRA licensing for data handling
- ADHICS compliance for healthcare data
- ISO 27001 certified data centers within Dubai/AUAE borders
Verify physical server locations to ensure data sovereignty under UAE Federal Law No. 2 of 2019. Enterprise solutions offer legally binding DPAs guaranteeing jurisdiction.
2. Enforce End-to-End Encryption Protocols
Standard TLS is insufficient. Mandate:
- S/MIME or PGP email encryption for message-level security
- TLS 1.3 enforcement with strict cipher suites (AES-256-GCM, ECDHE-RSA)
- Automated key rotation every 90 days
Implement zero-trust architectures where decryption occurs ONLY at endpoint devices, eliminating provider-side access. Hardware security modules (HSMs) in Dubai data centers provide FIPS 140-2 Level 3 key management.
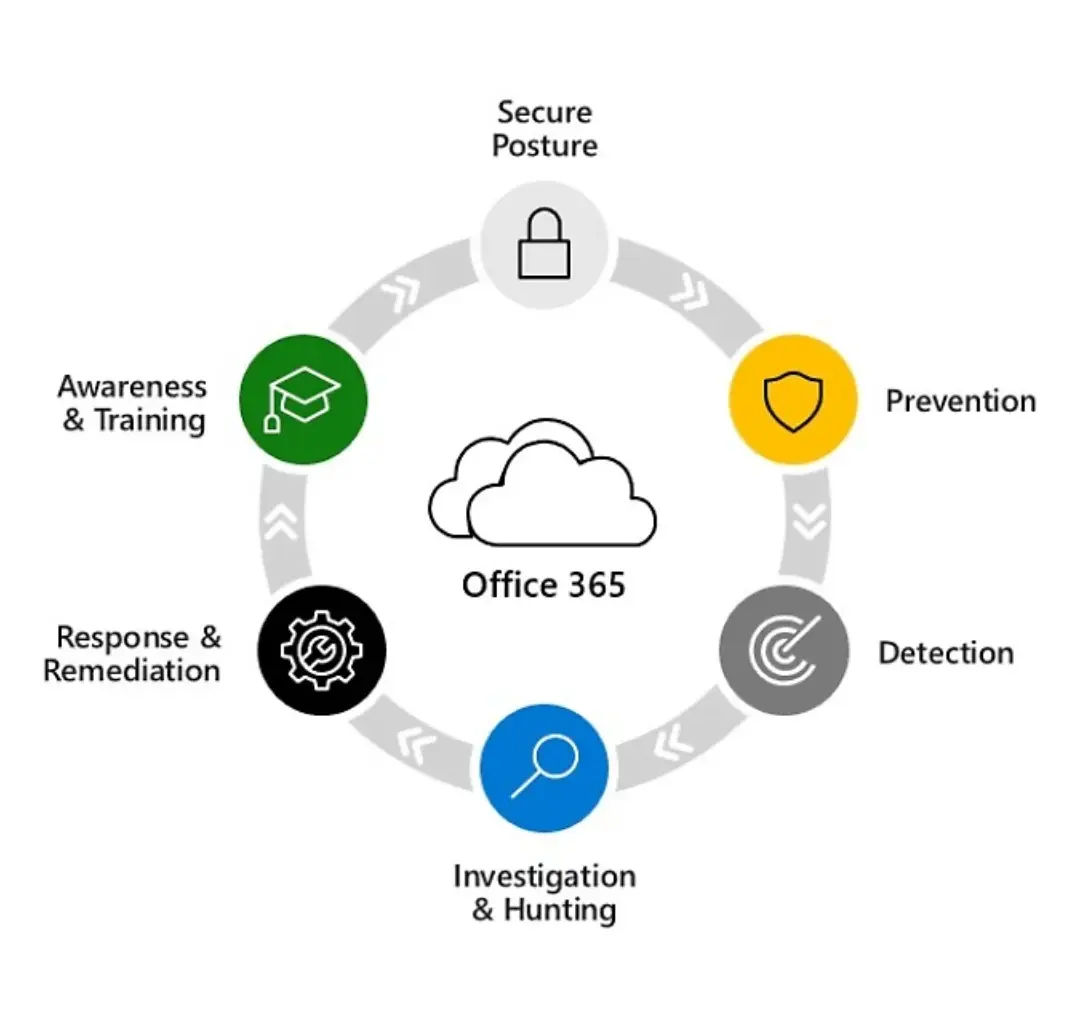
3. Deploy Advanced Threat Mitigation Layers
Leverage region-specific security stacks:
- Sandboxed attachment analysis at UAE network edges
- AI-powered sender verification detecting Business Email Compromise (BEC) patterns
- Real-time outbound email scanning preventing data exfiltration
Configure strict DMARC policies (p=reject) with forensic reporting. Maintain immutable audit trails meeting UAE Central Bank cybersecurity requirements for financial transactions.
Critical Implementation Note: Conduct quarterly TRA compliance audits and penetration tests by Dubai-based CREST-certified firms. Update incident response playbooks to reflect UAE Cybercrime Law reporting timelines.